Understanding Function Modifiers in Solidity
#100DaysOfSolidity 020 "Function Modifiers"
📝 Solidity is a programming language specifically designed for writing smart contracts on the Ethereum blockchain. One of the powerful features of Solidity is the ability to use function modifiers. Function modifiers allow you to run code before and/or after a function call. They can be used to restrict access, validate inputs, and guard against reentrancy attacks. In this article, we will dive deep into function modifiers in Solidity and explore their various use cases.
🔒 Restricting Access with Modifiers
Modifiers can be used to restrict access to certain functions or operations within a smart contract. Let's take a look at the `FunctionModifier` contract as an example:
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.17;
contract FunctionModifier {
address public owner;
uint public x = 10;
bool public locked;
constructor() {
owner = msg.sender;
}
modifier onlyOwner() {
require(msg.sender == owner, "Not owner");
_;
}
// Rest of the contract...
}
In the `FunctionModifier` contract, the `onlyOwner` modifier is defined. This modifier checks that the caller of a function is the owner of the contract. If the condition fails, the function call will revert with the error message "Not owner." The underscore (`_`) symbol within the modifier indicates where the rest of the function code should be executed.
To apply the `onlyOwner` modifier to a function, you simply add it before the function definition:
```solidity
function changeOwner(address _newOwner) public onlyOwner {
owner = _newOwner;
}
```
Now, only the owner of the contract can call the `changeOwner` function and update the `owner` variable. This is a powerful way to enforce access control within your smart contracts and protect sensitive operations.
✅ Validating Inputs with Modifiers
Modifiers can also take inputs and perform validation on them. Let's consider the `validAddress` modifier in the `FunctionModifier` contract:
```solidity
modifier validAddress(address _addr) {
require(_addr != address(0), "Not valid address");
_;
}
```
This modifier ensures that the address passed in as an argument is not the zero address. If the condition fails, the function call will revert with the error message "Not valid address." The `_` symbol indicates where the rest of the function code should be executed.
To use the `validAddress` modifier, you include it as a parameter in the function definition:
```solidity
function changeOwner(address _newOwner) public onlyOwner validAddress(_newOwner) {
owner = _newOwner;
}
```
Now, before executing the `changeOwner` function, the `validAddress` modifier will validate the `_newOwner` address to ensure it is not the zero address. This helps prevent unintended operations and enhances the overall robustness of your smart contracts.
🔒⛔ Guarding Against Reentrancy Attacks
Reentrancy attacks occur when a malicious contract repeatedly calls back into the vulnerable contract before the previous call completes. This can lead to unexpected and potentially malicious behavior. Modifiers can be used to guard against such attacks by preventing reentrant function calls.
In the `FunctionModifier` contract, the `noReentrancy` modifier prevents a function from being called while it is still executing:
```solidity
modifier noReentrancy() {
require(!locked, "No reentrancy");
locked = true;
_;
locked = false;
}
```
The `locked` variable is used to track the reentrancy state. When a function
with the `noReentrancy` modifier is called, it checks if `locked` is `false`. If it's `true`, the function call will revert with the error message "No reentrancy." Otherwise, the `locked` state is set to `true`, the rest of the function code is executed (`_`), and finally, the `locked` state is reset to `false`.
Let's take a look at the `decrement` function in the `FunctionModifier` contract:
```solidity
function decrement(uint i) public noReentrancy {
x -= i;
if (i > 1) {
decrement(i - 1);
}
}
```
The `decrement` function subtracts `i` from the `x` variable. If `i` is greater than 1, the function recursively calls itself with `i - 1` as the argument. The `noReentrancy` modifier ensures that no reentrant calls can occur during the execution of the `decrement` function, preventing any potential reentrancy vulnerabilities.
📝💡 Educational Content and Sample Code
Solidity function modifiers are a powerful tool for enhancing the security and functionality of your smart contracts. They provide a way to enforce access control, validate inputs, and guard against reentrancy attacks. By using modifiers effectively, you can write more robust and secure smart contracts.
Here are a few additional code samples to further illustrate the usage of modifiers:
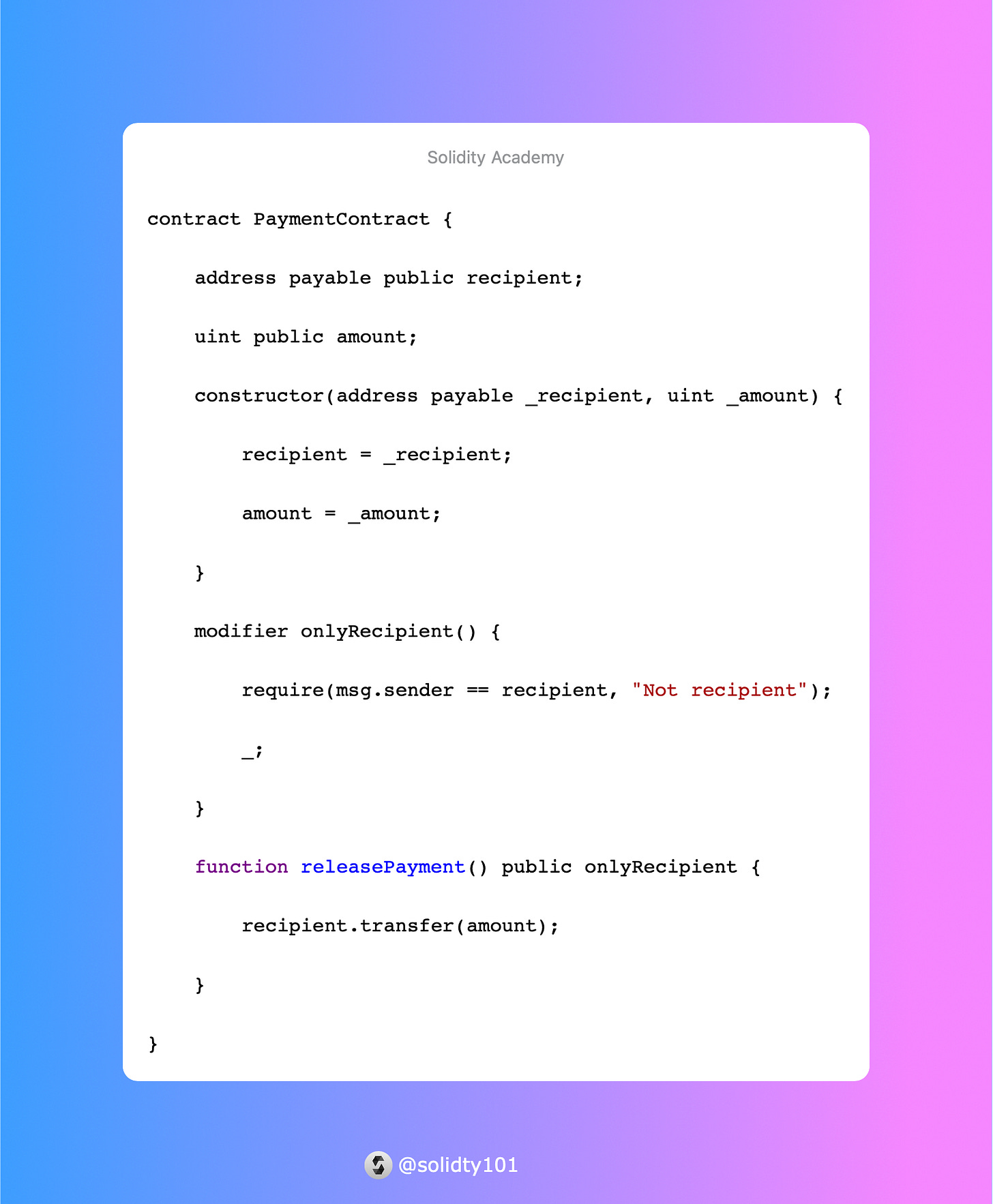
In the `PaymentContract` contract, the `onlyRecipient` modifier ensures that only the designated recipient can release the payment. This provides a simple access control mechanism for the `releasePayment` function.
Modifiers can also be combined to apply multiple conditions:
modifier validInput(uint _value) {
require(_value > 0, "Invalid value");
_;
}
modifier onlyPositiveBalance() {
require(address(this).balance > 0, "No balance");
_;
}
function withdraw(uint _value) public validInput(_value) onlyPositiveBalance {
// Withdraw logic...
}
In this example, the `withdraw` function can only be called with a positive value, and the contract must have a positive balance. These two modifiers work together to ensure a valid withdrawal operation.
🔍🔄 Analyzing and Comparing Smart Contracts
Now, let's analyze, compare, and comment on the smart contracts provided.
The `FunctionModifier` contract showcases the use of modifiers for access control (`onlyOwner`), input validation (`validAddress`), and guarding against reentrancy attacks (`noReentrancy`). These modifiers add an extra layer of security and control to the contract's functions.
By using the `onlyOwner` modifier, the contract restricts certain operations to the contract owner only. This prevents unauthorized access and ensures that critical functions can only be executed by the owner.
The `validAddress` modifier helps prevent the use of invalid addresses, which can lead to unexpected behavior or loss of funds. This validation ensures that operations involving addresses are executed with valid inputs.
The `noReentrancy` modifier protects against reentrancy attacks by locking the function during execution. This prevents any potential recursive calls that may exploit vulnerable state changes.
Overall, the `FunctionModifier` contract demonstrates good practices for access control, input validation, and protection against reentrancy attacks. It provides a solid foundation for building secure and reliable smart contracts.
📚 Conclusion
Function modifiers are a valuable feature in Solidity that allow you to enhance the security and functionality of your smart contracts. They enable you to enforce access control, validate inputs, and guard against reentrancy attacks. By using modifiers effectively, you can write more robust and secure smart contracts on the Ethereum blockchain.
In this article, we explored the concept of function modifiers in Solidity and provided detailed explanations and code samples. We discussed the use of modifiers for access control, input validation, and protection against reentrancy attacks. Additionally, we analyzed and commented on the `FunctionModifier` contract, highlighting its secure design.
Remember to leverage function modifiers in your smart contract development to create more secure and reliable applications on the blockchain. Happy coding! 👨💻💡